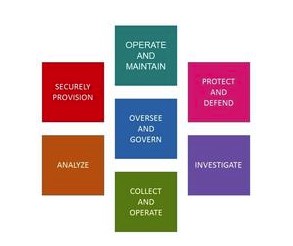
One of the greatest hindrances to mitigating cybercrime is the lack of qualified and skilled professionals trained in cybersecurity.
Cybersecurity is a rising career field with a need for more security professionals in all industries and types of organizations. One of the greatest hindrances to mitigating cybercrime is the lack of qualified and skilled professionals trained in cybersecurity. Companies are looking to fill these roles. And there are numerous people interested in entering the field. There are three categories of people interested in joining the fight:
- Young professionals starting their careers
- Experienced professionals moving from one career into cybersecurity
- Professionals at all levels wanting to learn more about it to better protect their personal and business lives.
All three begin with the question: where do I start my learning about cybersecurity?
Where to start a cybersecurity learning journey
If you’re wondering where to start in cybersecurity, start with CompTIA Security+. Out of the many security certs out there, it’s the easiest route to get certified and learn more about the technologies and business of cybersecurity.
The CompTIA Security+ SY0-501 exam is an internationally recognized validation of foundation-level security skills and knowledge and is used by organizations and security professionals around the globe. This certification proves an IT security professional’s competency in topics such as threats, vulnerabilities, and attacks, system security, network infrastructure, access control, cryptography, risk management, and organizational security.
 Courses such as the Cybrary Cybrary Security+ video series covers these topics to prepare students for the CompTIA Security+ SY0-501 certification exam. The fundamentals taught in this class will help you get started in a career as a cybersecurity analyst and build your security knowledge base.
Courses such as the Cybrary Cybrary Security+ video series covers these topics to prepare students for the CompTIA Security+ SY0-501 certification exam. The fundamentals taught in this class will help you get started in a career as a cybersecurity analyst and build your security knowledge base.
For those entering or even moving around the career, you should understand the many job roles available and find the one that best fits you. The Cyber Seek website (https://www.cyberseek.org/pathway.html) contains a list of careers. It provides an interactive career pathway of key jobs within cybersecurity, common transition opportunities between them, and detailed information about the salaries, credentials, and skillsets associated with each role.
The journey is more important than the destination
With CompTIA Security+ or any certification, note that the journey is more important than the destination. The goal is not simply gaining a certification and letters after your name, but understanding all aspects of a complex and wide career field. Studying for a certification is often the start of your learning about cybersecurity. It expands your mind and helps you see the entire playing field required of cybersecurity analysts. It also lets you know about your strengths and weaknesses, since it’s near impossible to know everything about all areas of cybersecurity. For example, if you enjoy the technical aspects, then you should look at being a security administrator, pen tester, or forensics analyst. If business is more your forte, you should focus on policy, governance, compliance and risk. The certification journey helps you determine your focus areas so you can have maximum effectiveness, no matter your career choice.
Benefits of certifications
Certifications establish your credibility in the industry and open doors for jobs.
Certifications establish your credibility in the industry and open doors for jobs. It’s often the first thing requested in job descriptions. Certifications show you have knowledge in a specific area or indicates that you have the subject matter expertise and that you’ve taken the effort to obtain and maintain it.
If you’re starting your cybersecurity journey, look to the CompTIA Security+ as the place to jumpstart your career and gain critical knowledge in protecting your personal life, your organization and ultimately everyone.
For more information about Cybersecurity careers, see my previous Peerlyst blogs:
- Choosing Your Cybersecurity Career Path: https://www.peerlyst.com/posts/choosing-your-cybersecurity-career-path-ron-woerner
- Breaking into Security Careers – 2018: https://www.peerlyst.com/posts/breaking-into-security-careers-2018-ron-woerner
I’d love to hear from you about your experiences with cybersecurity certifications as part of your career journey.



 This is just a short tutorial on building your cybersecurity career. Like in the Matrix, you need to pick a path (the red pill or the blue pill / strategic or tactical / education or certification) and move towards your goals.
This is just a short tutorial on building your cybersecurity career. Like in the Matrix, you need to pick a path (the red pill or the blue pill / strategic or tactical / education or certification) and move towards your goals.
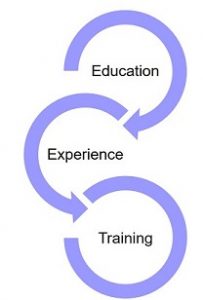 1. Education: With education, you learn how to learn. Cybersecurity is a vast field and it’s nearly impossible to know everything. You need to be able to learn and adapt quickly to new technologies, situations, and processes. Education also builds the soft skills of critical thinking and communications. It’s readily available both online and in-person through local universities and training partners like
1. Education: With education, you learn how to learn. Cybersecurity is a vast field and it’s nearly impossible to know everything. You need to be able to learn and adapt quickly to new technologies, situations, and processes. Education also builds the soft skills of critical thinking and communications. It’s readily available both online and in-person through local universities and training partners like